Last week I posted a blog about the Remote Desktop Client on Windows 8, in which I promised to write a follow up post on Remote Desktop Services in Windows Server 8. So here it is. In this blog post, I will focus on the new Scenario Based Deployment of Remote Desktop Services, which is new in Windows Server 8.
The following servers are running within my lab.local environment (all Windows Server 8 developer edition x64).hostname | roles |
RDSH-WIN8-001 | Desired role on this machine will be Remote Desktop Session Host (RDSH) |
RDGWWA-WIN8 | Desired roles on this machine will be Remote Desktop Gateway and Remote Desktop Web Access* |
RDCB-WIN8 | Desired role on this machine will be Remote Desktop Connection Broker |
When we logon to a Windows Server 8 for the first time we’re presented with the new Server Manager Dashboard, which looks pretty smooth.
Before we can start our Scenario Based Deployment the Server Manager needs to know what servers you want to manage, and thus install roles on. If you forget this step you won’t be able to select other servers later on in the wizard than the local host that you are running the wizard on. So don’t forget this step! We select Add other servers to manager (option 3) and are presented with the following dialog.We can browse the Active Directory to add servers. Since we know that all the servers that we want to join to this scenario start with “RD” we filter on this text, add the three servers in question, and click finish.
Note that the Server Manager Dashboard now shows the servers we can manage from Server Manager. (See below)
We’re now ready to start our Scenario Based Deployment of RDS.
Since we are going to be installing roles we choose (option 2) add roles.
We are presented with the screen below which is the improved Add Roles and Features Wizard. New in this wizard is that the destination server is show in the upper-right corner. This is because we also have the ability to use this GUI to install roles on remote servers.
We click Next to start the wizard and we’re presented with the screen below.
This brings us to the topic of this blog, the Scenario Based Installation. As explained earlier, this installation type is only available for Remote Desktop Services. (At least in the Developer preview edition). We obviously select Scenario-based Installation and click Next.
Here we have two options. We can choose either a Standard or Quick Deployment. The Quick Deployment option can be used for a single server deployment of Session Virtualization and/or Virtual Desktop Infrastructure. In this case, we want to deploy RDS over multiple servers so we’re going to stick with the Standard deployment. Also note that the previous screens showed the destination server in the upper-right corner. Because we selected a scenario-based installation in the previous dialog we (might) setup RDS over multiple servers which we select later on so the destination server reverts back to No Servers Selected.
In the Select deployment Scenario dialog we again have two options, a VDI or RDS deployment. As you might have guessed we will choose Session Virtualization deployment here (which is RDS).
This dialog sums up the different roles that the wizard is able to deploy including links to additional information per role. Notice that the Remote Desktop Gateway (RDGW) is not part of this Scenario Based deployment. We click next.
The Select RD Connection Broker dialog is used to select the servers that we want to install the RCCB role on. We select the RDCB-WIN8 server and click Next.
On the Select RD Web Access dialog, we have to option to select servers that we want to install the RDWA role on. Note that we have the option to install RD Web Access on the same server as the RD Connection Broker. We choose RDGWWA-WIN8 as the server and click Next.
The Select RD Session Host Servers dialog is used to select the servers that we want to install the RDSH role on. We select the RDSH-WIN8 server and click Next.
The last step of the deployment is the Confirmation dialog. This shows a summary of the different roles that we will be deploying and the machines that we’re deploying these roles on. Note the warning that the server that we install the Remote Desktop Session Host role on needs to be restarted afterwards. (Which is not new compared to Window Server 2008 (R2). We confirm the restart the of RDSH servers by selecting the option and click Deploy.
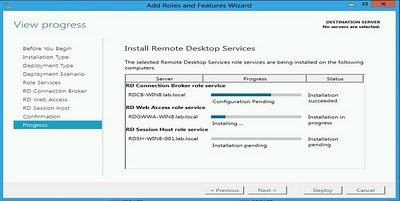
Using the progress dialog that is now shown we can follow the progress of the scenario based deployment.
As we can see later on, the wizard reboots the RDSH server as promised.
I was surprised to see the next dialog that shows a failure.
Apparently, the wizard wants to enable Remote Connections to the all servers using SetAllowTSConnections method. I’m guessing that this refers to this; http://msdn.microsoft.com/en-us/library/Aa383644. I had configured to allow Remote Access to de machines via a GPO setting prior to running this wizard so perhaps the failure is shown because Remote Access is already allowed. What does surprise me is the fact that the wizard also wants to configure Remote Access on the RDWA and RDCB besides the enabling this in the RDSH.
Anyhow, the server manager now has an additional tab Remote Desktop Services. I’ve checked the servers separately and they have the roles installed exactly as expected. Where needed, the prerequisites (like i.e. IIS for RD WebAccess) have also been installed.
This makes the scenario based deployment of Remote Desktop Services complete and successful! The next step will be to further explore the configuration of the separate RDS roles. I’ll devote another post on this subject soon!
To be continued…



























